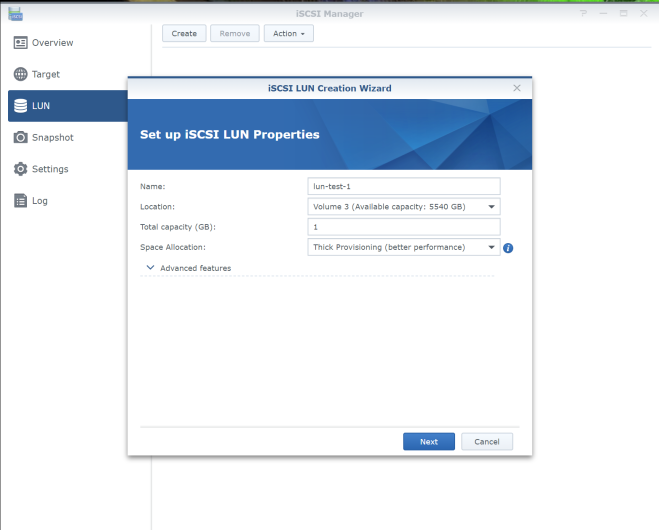
My experiences of buying camera gear on eBay
Some context
Disclaimer: Looking back, the limitations I had weren’t with my camera, but were with the 18-270 Tamron lens in low light conditions, and my ability to understand the limitations of a variable aperture lens in low light.
Things I look for when buying a camera on eBay
The shutter count/number of actuations
When looking at a camera, this is one thing that is likely to influence the price. Before going any further, it’s worth understanding why people obsess over it so much.
In summary, the shutter is a mechanical component that will wear out over time. It happens. It’s also the case that it’s something that’s hard (if not impossible) to replace yourself. Having said this, it actually means that the higher shutter count, the more chance there is of the shutter failing. This number will vary between cameras, and I strongly suggest you check somewhere like here (for my d810) to check what the chances of failure are at a particular shutter count.
http://www.olegkikin.com/shutterlife/nikon_d810.htm
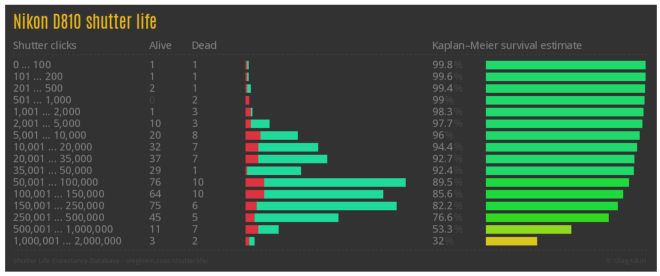
Looking at the example of a d810, I probably wouldn’t buy one with 150’000 actuations, but I wouldn’t think twice about picking up one with 20’000 actuations.
A big caveat to this is if it’s been replaced and has supporting paperwork.
Condition of the body
Another thing when buying a second-hand body is “how well has it been treated in a previous life”?
I care because if someone has looked after the body, drying it off after it’s been in the rain, washing corrosive salt spray off the body, and repairing broken rubber grips tells me the last owner cared about it. I can make a reasonable expectation that they have probably put it in a well-padded bag, or even that it’s just been stored away and not used very much. These are things I look for.
Boxes, and paperwork
A camera that’s had a hard life isn’t always a bad thing, you can get some great deals on ex-pro equipment, and if there is good paperwork to back it up, then that is definitely worth looking at. Loved ex-pro gear is great. If they have the boxes, that will help any resale and is pretty positive when buying.
Grey Imports
- No official in-country warranty
- No deals/ rebates
- Lower resale value
- In some countries, you’ll struggle to get it repaired as “official repair shops” won’t touch it under threat from the manufacturer
In the UK, we have a wonderful company called Fixation who just repair things. Give them a call if you are unsure https://www.fixationuk.com/
Note: I have no connection with them, other than being a huge fan and a customer.
Bidding, offers and buy it now
So to keep it simple, you should know what an item is worth when you look for it.
Bidding
Bidding provides the biggest chance of getting a good deal, just have a ceiling price in advance and do not go above it. The last 60 seconds is the only time that matters. Do not chase an item, ever.
Offers
Making offers has been a really good way of getting gear at a good price. You are taking the hassle and delay away from the seller, but annoying them with under par prices will get you ignored pretty quickly.
Buy it now
If an item is on at a decent price for buy it now, check very carefully why. If it’s a commercial seller, they will be making a profit somewhere. Make sure you aren’t paying too much, or that the product has some small print that says “for spares only”.
Know what it costs elsewhere
Things I look for when buying a Lens on eBay
- Know exactly what you are looking for, know the age of the lens and common issues with those lenses.
- Look for worn lettering around the barrel (which doesn’t mean for sure, but may indicate heavy/pro usage). If this is the case, ask for some detail around servicing paperwork. Nothing wrong with a well-used lens if it’s been loved.
- Look for the magic words “no fungus, optically perfect”. If you see this, it means you have some recourse if that turns out not to be the case.
- Personally, I look for the original box and accessories because it makes resale easier if I choose to ditch it.
- Check the postage and understand how it’ll be transported. You want absolute clarity if it doesn’t arrive. Offer to pay for better carriage if it’s going to save you having a broken lens.
- Where is it being transported from? If it’s in your own country, you may be better picking it up personally.
- Please feel free to disagree here, but there is a lot less to go wrong with a prime, than a zoom, or something with VR.
- Know what a new grey market lens would cost. Second hand Nikon 24-70 f2.8 was going for £1400 on eBay, £1299 shipped from Digital rev.
- Know where you can get them repaired even if out of warranty/grey. In the UK we are lucky to have fixation who repair anything. https://www.fixationuk.com/